The Ministry of Justice / Cabinet Office have produced a public consultation Green Paper on Justice and Security. which closes on 6th January 201.
Some Spy Blog observations on:
Nobbling civil cases and inquests
The first section seems to be about various proposed legalistic fiddles to the evidence procedures civil cases and Inquests.
They seem to be proposing to infect civil courts and inquests with the same wretched Special Advocate / Closed Material Procedures schemes which were introduced under Labour for the ineffective Special Immigrations Appeals Tribunal (SIAC) and the Proscribed Organisations Appeal Commission (which rarely does anything at all).
They also appear to be trying to nobble the use of Norwich Pharmacal orders (a rarely used legal precedent which allows a third party not directly involved in a civil case, to be ordered to hand over information or evidence which is pertinent). Such orders have recently been applied to cases tainted with "national security" or "intelligence" rather than actual evidence.
If you believe the Green Paper, this is to allow better, more accurate "justice" in cases cases which involve genuine "national security" secrets, which might otherwise have to be abandoned or settled out of court by the government to preserve "the public interest" in secrecy.
The increasingly hated and incompetent previous Labour government always cloaked its repressive legislative onslaught on our civil liberties and freedoms with Orwellian newspeak and the Coalition seems to be following suit.
Whilst there is a case for keeping genuine time limited tactical intelligence, or the specific details of still viable technological intelligence gathering techniques, or the identities of Covert Human Intelligence Sources secret, there is no trustworthy mechanism for limiting such secrecy only to such examples.
Far too often, the "national security" classification of documents or witness testimony is really about preventing embarrassment to politicians, mandarins and apparatchiki in Whitehall etc.e.g. the torture claims case of Binyam Mohamed and the inquest into the "Friendly Fire" deaths of UK military personnel caused by trigger happy US Air Force ground attack aircraft pilots in Afghanistan etc.
It is all about maintaining the fiction of the appearance of "The Control Principle"
We expect our intelligence partners to protect our material when we share it with them, and we must be able to deliver the same protection of their material.
Confidence built up over many years can all too quickly be undermined. That is why, if the trust of the UK's foreign 'liaison' partners is to be maintained, there should be no disclosure of the content or fact of the intelligence exchange with them without their consent. This is known as the Control Principle.
The United States government, for example, regularly betrays this Control Principle, either through incompetence, or when it suits them politically e.g.
- Leaving Diplomatic Cables involving the United Kingdom or our allies on vulnerable computer systems accessible by millions of low level US military personnel, bureaucrats and defence contractors, to then be published "for maximum impact" by the Wikileaks.org cult.
- Several UK anti-terrorism raids involving international plots, have had to be rushed too early, before the alleged plotters have actually got their hands on any explosives or weapons or money etc.because the US government crowed about them in public, thereby perhaps tipping off some of the suspects.
Is this Control Principle going to be applied to all of the secret MI6 correspondence recently retrieved by journalists and human rights activists from abandoned government offices in Libya ?
In the Binyam Mohamed case, which is what led directly to the still not yet properly running Detainee Inquiry on UK Government complicity in torture, the "intelligence material" details in dispute had already been made public in the USA, but the UK government persisted in wasting public money on legal appeals to pretend to be upholding the "Control Principle".
Still no proposals about Intercept As Evidence
A major failing of this Green Paper is the lack of anything about the policy of No Intercept As Evidence.
This is Yet Another Broken Promise by the Coalition government - both the Conservatives and the Liberal Democrats claimed that they would sort this out, when making thei increasingly worthless pre-election promises. The Labour party, is as usual, failing to hold the government to account, presumably because they dare not remind people of their own repressive mendacity.
Whitehall is still dithering about this after all these years, with the "Advisory Group of Privy Counsellors" chaired by Sir John Chilcot, not actively doing anything about it, as he is presumably busy giving the likes of Tony Blair etc. an easy time of it over at the still running Iraq Inquiry anyway. - see the previous Spy Blog article Intercept as Evidence Report - £2.5 million spent and still no workable "legal model"
Intelligence and Security Committee
The slightly more interesting section is on proposed reforms to the Intelligence and Security Committee and the Regulation of Investigatory Powers Act 2000 Commissioners - The Intelligence Services Commissioner and the Interception of Communications Commissioner
All of these suffer from a lack of public visibility amongst the general public and a vast amount of scepticism about their effectiveness amongst those of us who do actually bother to read their censored public reports.
Question: What changes to the ISC could best improve the effectiveness and credibility of the Committee in overseeing the Government's intelligence activities?
3.4 The Government recognises the criticisms that have been made about current oversight arrangements, particularly that they do not provide sufficient public reassurance that current scrutiny is effective.
The Government does not want the ISC to have even the weak powers of a Select Committee
3.18 A possible option would be to change the status of the ISC to that of a departmental select committee. Departmental select committees have a remit 'to examine the expenditure, administration and policy' of the relevant government department and associated public bodies. A Standing Order, which would need to be renewed each Parliament, could cover appropriate handling of sensitive material, accommodation, staffing and reporting. Creating a select committee would result in oversight being demonstrably undertaken by Parliament.
3.19 However, under such arrangements the Government would clearly have no veto on publication of sensitive material.
That is the whole point !
There would be a real risk that, with fewer safeguards in place than under the present arrangements, Agency Heads would find it hard to reconcile their statutory duty to protect information with their statutory duty to facilitate parliamentary oversight.
Contempt of Parliament and contempt for the general public.
Sharing of less sensitive information and a corresponding reduction in both the credibility and effectiveness of the oversight the committee provided could be the result.
For these reasons, the Government believes this option should not be taken forward.
How can this be less effective or less credible than the current milksop that is the Intelligence and Security Committee ?
3.23 As the ISC has developed its role it has, with the agreement of previous and current governments, taken evidence from bodies beyond the three Agencies which are a part of the wider intelligence community within government These include Defence Intelligence in the Ministry of Defence (MOD), the Office for Security and Counter-Terrorism in the Home Office and the central government intelligence machinery in the
Cabinet Office (including the Joint Intelligence Organisation). It has also, in its annual reports, made recommendations relating to those bodies. The ISC has proposed that this role should be formalised.
3.24 These bodies are part of larger departments (MOD, Cabinet Office and Home Office) which are overseen by the appropriate departmental select committee. However, where the work of these organisations relates directly to intelligence material, the relevant departmental select committees are not able to provide oversight. The Government proposes formally to recognise the wider role the ISC should play in overseeing the Government's intelligence activities by enabling it to take evidence from any department or body in the wider intelligence community about intelligence-related activity where to do so would help the ISC provides coherent intelligence oversight. This development would not affect the primary accountability of those bodies to the relevant departmental select committee of the House of Commons.
It is obvious that even Members of the Select Committee on Defence, like the Liberal Democrat MP Mike Hancock are not actually trusted with any secrets:
Why is Sir Stephen Lander (ex DG of MI5) involved in the SIAC deportation case of Katia Zatuliveter ?
However, what in the USA would be the criminal act of acting as an Unregistered Agent of a Foreign Government, is tolerated and encouraged by UK Ministers and top Civil Service mandarins, when it comes to commercial or political lobbyists as revealed in the Liam Fox / Adam Werrity scandal.
Accommodation, staffing and budget
3.31 We are considering possible changes to the ISC's staffing, accommodation and funding with a view to strengthening both the ISC's actual and symbolic connection to Parliament. The most tangible physical demonstration of independence, and a natural consequence of the ISC becoming a Committee of Parliament, would be to make
arrangements with the parliamentary authorities for the ISC to be accommodated in suitably secure premises on the parliamentary estate, rather than on the government estate. Similarly, its staff could have the status of parliamentary staff (rather than departmental civil servants based in the Cabinet Office), and its budget funded directly from parliamentary appropriation rather than the Cabinet Office's departmental budget.
3.32 The Government accepts that some of the proposals in this section, if implemented, would require a modest uplift in the Committee's current levels of resourcing. The ISC itself has made a case for an increase in its resourcing. Following decisions on next steps after this consultation, the Government - with the parliamentary authorities if the above plans are taken forward - proposes to review the level of resourcing that the ISC requires to support it in the discharge of its functions and the nature of the skills the Committee requires to have at its disposal.
How about an actual Investigative team with access to scientific forensic techniques for examining paper and computer documents ?
How about some forensic accountants who can "follow the money" any suspected trail of waste and corruption involving secret projects ?
How about proper secure and anonymous electronic and physical communications facilities, which the UK intelligence agencies are expressly forbidden from snooping on ?
How about a comprehensive intelligence agency whistleblower protection scheme backed up by criminal sanctions, to encourage internal whistleblowers who may have important allegations or evidence to bring forward to the ISC, without the fear of being detected or punished by their work colleagues or bosses.
See Spy Blog letter to the Detainee Inquiry re: lack of whistleblower anonymity protection and immunity from prosecution
Access to information
3.36 Under current legislation the ISC requests information from the Heads of the three Agencies who can, in theory, decline to disclose information if it is 'sensitive' (as defined by ISA - which could include information about sources or methods or relating to articular operations or which has been provided by foreign partners who do not consent to its onward disclosure). An Agency Head's refusal to disclose such information to the ISC can be overturned by the relevant Secretary of State on public interest grounds. In practice,
Agency Heads have rarely refused an ISC request for information.
The fact that they have actually done so repeatedly in the past, has been revealed in the public section of several of the ISC's censored Annual Reports.
The Government agrees with the ISC's proposal that the Committee should be given the power to require information from the intelligence Agencies. The Government also agrees with the ISC proposal that this should be subject only to a veto exercisable by the relevant Secretary of State, rather than by the Head of the individual Agency, as now.
About time too, although what actual difference the location of the exercise of such a veto will actually make in practice, remains to be seen.
Raising the public profile of a couple of the RIPA Commissioners
The Commissioners
The role of the Commissioners in intelligence oversight
3.39 Independent oversight of the Agencies is provided by the Intelligence Services Commissioner and the Interception of Communications Commissioner. The Commissioners are appointed by the Prime Minister for a (renewable) period of three years and must hold or have held high judicial office.
The Intelligence Services Commissioner's central function is to keep under review the issue of warrants by the Secretary of State, including those authorising intrusive surveillance (e.g. eavesdropping) and interference with property, in order to make sure that the Secretary of State's issue of the warrants was in compliance with legal requirements. The Interception of Communications Commissioner's central function is to keep under review the issue of warrants for the interception of communications. More details of the remits of the Commissioners can be found at Appendix G.
3.43 The Government proposes that the Commissioners' ability to discharge these types of duties is placed on a statutory footing, in order to ensure transparency, coherence and a clear basis of authority. This would need to be broad enough to cover current non-statutory duties and also a range of potential future duties. The Government proposes that this is done by adding a general responsibility for overseeing the effectiveness of operational policies to the statutory remit of the Intelligence Services Commissioner, who would maintain responsibility for monitoring compliance by the Agencies with the necessary legal requirements in the exercise of their intrusive powers. The specific areas on which the Commissioner focuses at any one time would need to be agreed, on an ongoing basis, with the appropriate Secretary of State.
3.44 The effectiveness and value of the Commissioners in providing assurance and challenge to Ministers is not in doubt.
Yes there is plenty of doubt !
They are highly respected former members of the judiciary whose experience and insight is invaluable in checking the necessity and proportionality of the use of the Agencies' intrusive powers. However, their low public profile means that they play a lesser role in providing assurance to the general public that the activities of the Agencies are at all times reasonable, proportionate, necessary and compliant with all legal obligations. A number of steps have been taken recently to increase the public profile of the Commissioners. The Commissioners' most recent annual reports have been revised to make them more readable and with the inclusion of more qualitative information of potential interest to readers. A new dedicated website for the Commissioners has been established and is expected to go-live around the time of publication of this Paper. These steps are important as they allow the Commissioners to explain to the public how their offices work, what they do and how they link into other elements of the oversight landscape. The Government considers that future appointments should bear in mind the importance of the public element of the Commissioner role.
This "new dedicated website for the Commissioners " got off to a typically inept start:
MI5 inspector's website shut down after security blunder
A new website for the former High Court judges responsible for oversight of MI5, MI6 and wiretapping has been shut down after it emerged that anyone could edit any page of it.
By Christopher Williams, Technology Correspondent
8:00AM BST 23 Oct 2011
The security blunder forced the Intelligence Services Commissioner, Sir Mark Waller, and the Interception of Communications Commissioner, Sir Paul Kennedy, to pull the plug on their new website on Friday afternoon following enquiries by The Telegraph.
Every page contained an "edit" link that allowed anyone visiting the website to change any text and upload files.
After it was shut down a secure version was published at a new address
[...]
The secure version of their new website is at
www.intelligencecommissioners.com.
Inspector General
The Government have also floated the idea of an Inspector General, but their proposal in Appendix I is rather half hearted:
Question: Are more far-reaching intelligence oversight reform proposals preferable, for instance through the creation of an Inspector-General?
Appendix I
Possible model for an Inspector-General
1. An Inspector-General (IG) could oversee the powers and policies of the security and intelligence agencies and retrospectively review their operational activity. An IG for the Agencies could replace the Intelligence Services Commissioner and part of the remit of the Interception of Communications Commissioner.
2. An IG could be responsible for oversight of all the Agencies' covert investigation techniques, including the use of authorisations under the Intelligence Services Act 1994, and use by the Agencies of powers under the Regulation of Investigatory Powers Act 2000 (RIPA) Part I Chapter I (interception) and Chapter II (communications data), Part II (surveillance and CHIS) and Part III (encrypted data). It could also be responsible for oversight of requirements arising out of new government policies or legislation or the development of new practices. The IG could also provide legal advice and guidance to the Agencies on the use of their covert investigative techniques.
Doesn't the existing role of Intelligence Services Commissioner already do this ?
3. An IG could review the policies and procedures of the Agencies that relate to operational activities, including ethical matters. Ethical matters could be referred from, and reviewed, in close co-operation with the Staff Counsellor.
Who are these Staff Counsellors to which intelligence agency whistleblowers could complain to regarding, say, ethical concerns they have about intelligence operations involving torture or excessive snooping on innocent people ?
Rt. Hon. Sir John Chilcot "was Staff Counsellor to the Security and Intelligence Agencies (1999-2004) and the National Criminal Intelligence Service (2002-06). "
What a small, cosy world there seems to be amongst senior Whitehall mandarins and Judges, even after they retire.
If you were a whistleblower within these organisations today, would you trust
- The personal integrity of such a former Whitehall mandarin or retired senior Judge - probably yes
- His Operational Security technical computer, communications and "Moscow rules" style anti-surveillance tradecraft, to keep your identity secret from your work colleagues and managers and from other intelligence agencies - almost certainly not
4. An IG could have a retrospective review function that would include the ability to launch its own enquiries into past Agency operational activity. It could have a right to request intelligence, subject to Ministerial veto.
That would be a change from the current RIPA only remit of the intelligence Services Commissioner.
5. This would create two distinct oversight bodies: one focused on the Agencies, and one on all other public authorities with RIPA powers.
The risk of this approach is that oversight of interception would be split between two different bodies, possibly leading to different standards or approaches emerging. This would need to be managed and would not necessarily be straightforward.
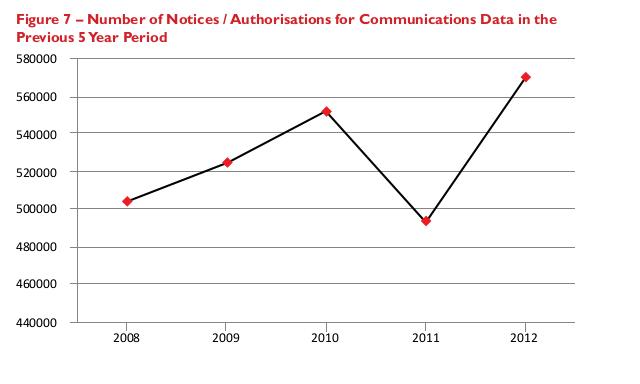
Oversight of Interception is not as much of a problem as the lack of proper oversight of the vastly larger number of requests / demands for Communications Data, something which the existing Interception of Communications Commissioner fails to satisfy the demand for public accountability.
6. The IG could have a statutory duty to consult the Prime Minister on its annual work programme. It could produce an annual report for the Prime Minister, and publish reports on the outcome of the retrospective enquiries into Agency operational activity and reviews into operational policies. The IG could have a duty to develop an effective public profile for its work.
There must be clear, very effective methods for members of the public and for whistleblowers to contact the Inspector General , securely and anonymously, in the first instance, without the technical or legal risk of being snooped by the very intelligence agencies that they might be complaining about or about which they are providing evidence of wrongdoing or incompetence or corruption etc.
A single, censored, RIPA Commissioner or Intelligence Security Committee style Annual report to the Prime Minister absolutely will not inspire any public or even Parliamentary confidence whatsoever.
Any such reports should be made directly to Parliament, like the Information Commissioner.
7. An IG could be appointed by, and answerable to, the Prime Minister. The post could have some form of pre-appointment scrutiny by Parliament and/or could be advertised publicly. The role could be filled by a suitably experienced judge. If this was not a judicial appointment, the IG could be a senior civil servant but would need to be supported by a legal adviser with the appropriate legal and/or judicial experience. The IG could head up a team which would include a Secretariat and specialists with responsibility for aspects of the work of the IG (e.g. interception)
No! The post should be independent of the executive arm of government i.e. it should be an appointment by the Queen, just like a High Court Judge.
Spy Blog suggestions
Question: What combination of existing or reformed arrangements can best ensure credible, effective and flexible independent oversight of the activities of the intelligence community in order to meet the national security challenges of today and of the future?
Question: With the aim of achieving the right balance in the intelligence oversight system overall, what is the right emphasis between reform of parliamentary oversight and other independent oversight?
Question: What changes to the Commissioners' existing remit can best enhance the valuable role they play in intelligence oversight and ensure that their role will continue to be effective for the future? How can their role be made more public facing?
A few Spy Blog suggestions which apply to the RIPA Commissioners or the proposed Inspector General and to the supposedly beefed up Intelligence and Security Committee
- How about some photos etc. of the Commissioners (or the Inspector General) on their website ? Like Sir Peter Gibson (ex Intelligence Services Commissioner) on the Detainee Inquiry website (if they can get the hang of Wordpress hosted in Amazon S3 cloud) ?

Rt. Hon. Sir Paul Kennedy, Interception of Communications Commissioner (photo UPPA Ltd via Daily Mail)

Rt. Hon. Sir Mark Waller, Intelligence Services Commissioner (photo via Serle Court Chambers)
- How about proper whistleblowing secure and anonymous contact web forms, email, postal address, mobile phones etc. for tip offs and whistleblowers ?
- Statutory whistleblower protection counteracting the exemptions to current "normal" employment, and the various "national security" legislation
- "Wilson Doctrine" extension to the Commissioners / Inspector General and the Intelligence and Security Committee and also their staff and families. This would apply to their public duties and to whistleblower related communications, but obviously not to investigations into private corruption etc.
- Criminal sanctions including prison and unlimited fines for breaches of these rules by the intelligence agencies or the police or private sector sub-contractors etc.
- Multi million pound budget and staff to handle enquiries from the public and the media - very cheap when compared to the lack of intelligence sources caused by mistrust of the agencies
- Inclusion within the Freedom of Information Act regime, with the proviso that most of the National Security exemptions will apply to most of their casework and investigations. However requests about the Commissioners / Inspector General offices themselves e.g. number of complaints, waiting time for complaints to be processed or investigated etc should be made public without question or delay.
- Statutory basis for the oversight of Prisons, which was lumped onto the Interception of Communications Commissioner by Gordon Brown, and which takes up a huge amount of his time and resources
Respond to the Consultation
Is it worth bothering to submit these to the formal Consultation process ?
There is an unencrypted web form:
http://consultation.cabinetoffice.gov.uk/justiceandsecurity/the-consultation
Email: justiceandsecurity@cabinet-office.x.gsi.gov.uk
Post: Justice and Security Consultation, Room 335, Cabinet Office, 70 Whitehall, London, SW1A 2AS
by Friday 6th January 2012

































Recent Comments